🐺 Dire Wolf Ransomware – Malware Analysis Report
1. Executive Summary
Dire Wolf is a newly emerged ransomware group first observed in May 2025. This double-extortion threat encrypts files and threatens to leak exfiltrated data to pressure victims into payment. The malware is written in Golang, packed with UPX, and employs anti-forensics, in-memory process execution, and aggressive termination of security-related services and processes to evade detection and disable defenses.
2. Malware Overview
- Name: Dire Wolf (aka Direwolf)
- Type: Golang-based Ransomware
- Discovery Date: May 2025
- Language: Go (Golang)
- Packing: UPX (Ultimate Packer for eXecutables)
- Execution: Direct Binary Execution
- Extortion Type: Double Extortion (Encryption + Leak)
- Targeted Sectors: Manufacturing, Technology, Finance, Healthcare
- Targeted Countries: US, Thailand, Taiwan, and 8 others
- Active Leak Site: Tor-hosted leak site + gofile.io
3. Infection & Execution Flow
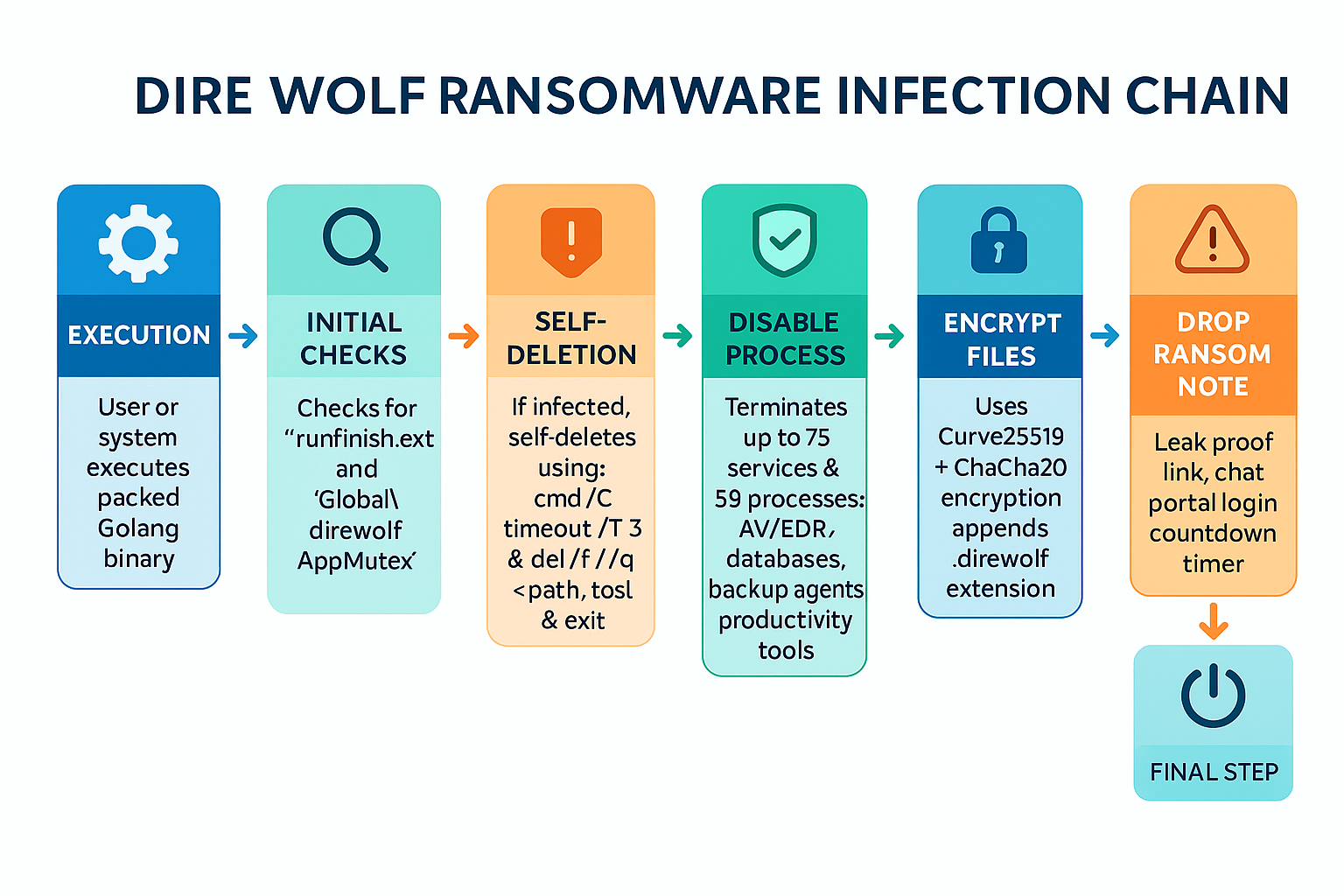
- User or system executes packed Golang binary
- Initial Checks:
- Checks for runfinish.exe marker file
- Checks for mutex Global\direwolfAppMutex
- If infected → Self-deletes using:
cmd /C timeout /T 3 & del /f /q <path_to_self> & exit - Disables Windows Event Logging via PowerShell and taskkill
- Terminates up to 75 services & 59 processes (AV, backups, DBs, productivity tools)
- Deletes backups and disables recovery using commands like vssadmin, wbadmin, bcdedit, and wevtutil
- Encrypts files (excludes system/critical files) using Curve25519 + ChaCha20
- Appends .direwolf extension
- Drops ransom note with leak proof link, chat portal login, and countdown timer
- Self-deletes and optionally reboots system
4. Static Analysis
- Packed With: UPX
- Written in Golang – cross-platform and AV-evasive
- Embedded Config:
- Mutex: Global\direwolfAppMutex
- runfinish.exe marker
- Victim-specific ransom portal credentials
- Leak proof sample links (e.g., gofile.io)
- Encryption targeting avoids critical files and existing .direwolf extensions
5. Dynamic Analysis
5.1 Backup & Recovery Destruction (Updated)
This function is responsible for removing backup options, disabling recovery mechanisms, and clearing event logs, to prevent forensic investigation or system restoration post-encryption. The following Windows commands are used:
vssadmin delete shadows /all /quiet – Deletes all volume shadow copieswmic shadowcopy delete /nointeractive –> Deletes shadow copies via WMIwbadmin stop job -quiet –> Stops any ongoing backup jobswbadmin disable backup -quiet –> Disables system backupswbadmin delete backup -keepVersions:0 -quiet –> Deletes all backupswbadmin DELETE SYSTEMSTATEBACKUP -keepVersions:0 -quiet –> Deletes system state backupswbadmin delete catalog -quiet –> Deletes backup catalog
These are followed by boot and recovery option modifications:
bcdedit /set {default} recoveryenabled No –> Disables Windows recovery environmentbcdedit /set {default} bootstatuspolicy ignoreallfailures –> Prevents recovery options from triggering on boot failure
Finally, the malware clears key event logs using wevtutil
wevtutil cl Applicationwevtutil cl Systemwevtutil cl Securitywevtutil cl Setupwevtutil cl "Microsoft-Windows-Windows Defender/Operational"
These actions make incident response and system recovery significantly more difficult, reinforcing Dire Wolf’s destructive capabilities before ransom negotiations.
5.2 Service & Process Termination
Stops and disables 75 hardcoded system services (AV, backups, DBs, etc.) and terminates 59 key processes repeatedly to disable defense and recovery tools.
6. Encryption Process
- Algorithm: Curve25519 (key exchange) + ChaCha20 (encryption)
- File Extension: .direwolf
- Exclusions: .exe,.dll, .sys, .tmp, .img, .iso, .direwolf
- Ransom Note includes victim-specific chat portal login, leak proof links, and countdown timer
7. Data Leak Site
- Leak Portal: Tor-hosted
- Victims Listed: 15 publicly as of June 2025
- Leak Staging:
- Phase 1: Sample data + file listing
- Phase 2: Full leak if ransom unpaid (~30 days)
- Claimed Origin: New York (unverified)
8. Indicators of Compromise (IOCs)
| Type | Value |
|---|---|
| Mutex | Global\direwolfAppMutex |
| File Marker | C:\runfinish.exe, xfssvccon.exe |
| Packed File Hash (data345.exe) |
MD5: A71dbf2e20c04da134f8be86ca93a619 SHA-1: Ed7c9fbd42605c790660df86b7ec325490f6d827 SHA-256: 8fdee53152ec985ffeeeda3d7a85852eb5c9902d2d480449421b4939b1904aad |
| Unpacked File Hash (data345.exe) |
MD5: aa62b3905be9b49551a07bc16eaad2ff SHA-1: 4a5852e9f9e20b243d8430b229e41b92949e4d69 SHA-256: 27d90611f005db3a25a4211cf8f69fb46097c6c374905d7207b30e87d296e1b3 |
9. Impact & Threat Landscape
- Active Countries: 11 confirmed (US, Thailand, Taiwan most affected)
- Victim Count: 16 confirmed as of June 2025
- Targeted Sectors: Manufacturing, Technology, Finance, Healthcare
- Ransom Demands: ~$250,000 to $2M USD
- Downtime per Victim: Estimated 3–7 days
- Data Exfiltration: PII, source code, financial docs, internal systems info
- Attribution: No confirmed actor, TTPs loosely resemble BlackCat/Cl0p
- Communication Channels: Live chat, qTox, personalized leak portals
MITRE ATT&CK Tactics & Techniques
- Initial Access: T1566.001 (Spearphishing Attachment), T1204.002 (Malicious File Execution)
- Execution: T1059.003 (Command Prompt), T1059.001 (PowerShell)
- Defense Evasion: T1089 (Disable Security Tools), T1489 (Stop Services), T1070.004 (File Deletion), T1562.001 (Modify/Disable Security Tools)
- Discovery: T1082 (System Info Discovery), T1057 (Process Discovery)
- Impact: T1486 (Data Encryption), T1490 (Inhibit Recovery), T1491.001 (Internal Defacement - ransom note)
10. Mitigation & Recommendations
- Endpoint Protection: Enable PowerShell ScriptBlock & Module logging; monitor shadow deletion & log clearing commands
- Backup & Recovery: Enforce offline/immutable backups; isolate from production; regularly test restores
- Network Defense: Block suspicious domains like gofile.io; segment networks; detect outbound Tor traffic
- Detection Engineering: Monitor creation of mutex Global\direwolfAppMutex, UPX-packed Golang binaries, and specific ransomware commands
11. Conclusion
Dire Wolf represents a sophisticated, financially motivated ransomware threat leveraging robust encryption, process manipulation, and double-extortion tactics. Its use of Golang, UPX packing, process/service termination, and self-deletion makes it elusive to traditional defenses. Early detection and proactive containment are crucial.